Your Harvest password is an incredibly important part of the defenses that keep your account safe. In the last few months, we’ve amped up our password security measures, giving your data more protection than ever.
Tighter Password Security
The way we handle passwords is safe and secure every step of the way.
Secure set-up
The Harvest Welcome Email includes a link to a secure password set-up screen. We’ll walk new users through a super-simple process that leaves no guesswork as to whether their password makes the grade.
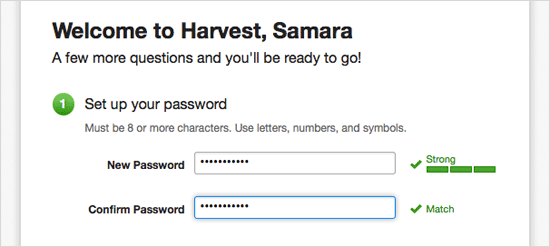
Safe reset
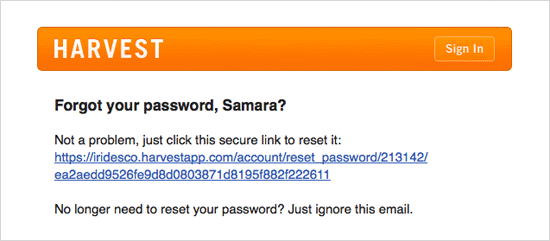
If you forget your password, we’ll email you a link to reset it. Your Harvest password is never visible in your account, and it is never sent over email.
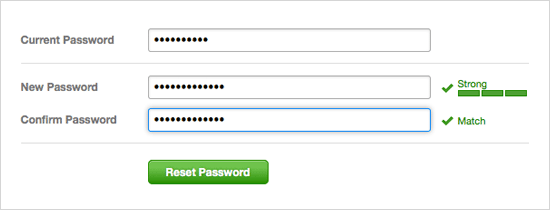
Strong requirements
We’ve tightened the belt on what you need – all new passwords must be at least 8 characters and receive a “Good” or “Strong” rating from our new strength indicator (you can try to save a weak password, but we won’t let you). Due for a new one? There’s no better time than now to update your password! Just head to the new Password section of your profile and take a few seconds to make yours more secure.
We know you’ve got a lot on your mind, but you can rest easy knowing that your Harvest account is safer than ever before. Stay tuned for more information on the ins-and-outs of password security, and don’t hesitate to send any feedback our way!













